You have a choice of several Signature Phrase Password options that apply to messages you are sending or reading. The Key Regeneration Assistant helps you to renew your existing encryption key before it is due to expire. If an email has sensitive information that needs to be encrypted, ZixVPM will automatically encrypt this email without the user having to do anything. Creating a Zix Signature: ZixMail for Outlook is a plug in for Microsoft Office Outlook that provides secure email delivery for individuals and organizations. You do not need to know if the recipients of your ZixMail messages have a ZixSignature. With ZixMail, you enjoy automated key management and leverage the ZixDirectory and Best Method of Delivery to exchange secure email with anyone, anywhere on any device.
| Uploader: | Akigal |
| Date Added: | 9 February 2007 |
| File Size: | 25.27 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 85638 |
| Price: | Free* [*Free Regsitration Required] |
Simply click on your email and enter your password to view encrypted email. Feel free to contribute!
The article is available here. We have an Exchange server which our employees connect to using OutlookOutlook. If they do, your messages are delivered via ZixGateway or ZixMail.
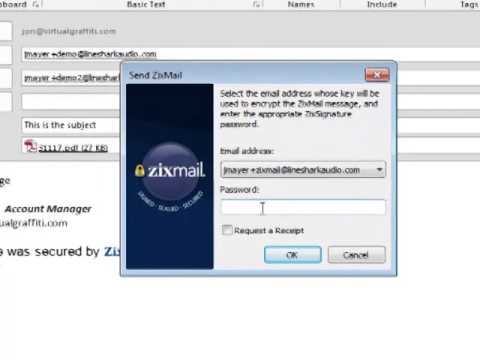
Privacy and security are becoming more important as business is increasingly being conducted online. Leave a Reply Cancel reply Your email address will not be published. I'll also look into the suggestions such as Virtru,ZixMail and NeoCertified and demo these as this will be. If you are unsure if your recipients have a ZixSignature, it is best to leave the default options selected, as this ensures that your messages will always be sent securely. The zixmail plugin will not work on a mac.
Users of the ZixVPM Virtual Private Messenger solution can send and receive encrypted email seamlessly without a password using Microsoft Outlook or another email client program.
This solution allows you to press the send secure button to encrypt any email.
Zixmail outlook download
Creating a Zix Signature: You can then read, reply, forward, save or delete your ZixMail message. Call a Specialist Today! In an effort to keep costs down zuxmail clients, BASIC recently requested a discount to be offered for our clients to increase their ability to use encrypted email communication. After completing this one-time 20010 process, you are ready to start sending and receiving ZixMail messages.
Click Finishedthen close ZixSignature Manager. It shows the best method of delivery, depending on the options you selected for the Message Encryption option.
End-to-End Email Encryption with ZixMail
Select a file location for the recovery file, then zixnail Next. The Key Regeneration Assistant helps you to renew your existing encryption key before it is due to expire. ZixMail Benefits ZixMail makes end-to-end email encryption easy, keeping customer data, employee records, financial information and other sensitive data secure both internally and externally.

You can select each check box to always allow:. Enter your existing email address, then enter it again to confirm. The password is case sensitive.
Zixmail outlook 2010
Remove any previous version of ZixMail before continuing with the install. In your email include your full company name and address as well as mentioning that you do business with BASIC. Maintaining end-to-end encryption, emails are encrypted in transit as zixmial as on your mail server.
Installed on your zixjail, ZixMail provides end-to-end email encryption to protect messages and attachments with a single click. The ZixSelect version for Outlookor file is located on the. Save my name, email, and website in this browser for the next time I comment.
Just take Microsoft Outlook for example, which is as well as in Outlook.
ZixMail Outlook Installation & Help | - Zix Premier Partner
Click Zixmal through the standard installation questions. You are taken to the Activation Successful page. How ZixMail Works ZixMail makes end-to-end email encryption easy, keeping customer data, employee records, financial information and other sensitive data secure both internally and externally.

Комментариев нет:
Отправить комментарий